What is a cyber attack?
In summary, the term “cyber attack” refers to any situation in which a hacker, or group, attempts to compromise a computer system, network, or device in an attempt to cause harm.
These attacks target governments and businesses as well as online users. They vary in nature and have different ways of inflicting damage.
We can separate them into two main categories:
- Attacks that aim to paralyze a system, or even deactivate it.
- Attacks aimed at obtaining access to a system and/or its data.
These two categories fall into several types of cyber attacks, which we'll look at in detail in the next section.
The attacks we are about to discuss are probably the biggest threat to humanity right now. Even more so than nuclear weapons, as Warren Buffet pointed out.
This is all the more reason to dig a little deeper and see the reasons for these harmful activities. I will explain why the attacks are taking place, who is carrying out them and who their victims are.
Why do cyber attacks happen?
1. Argent
This is the first reason why hackers invent new ways to access a system. The numbers are, as you might expect, breathtaking!
Cybersecurity attacks will cost the global economy up to 6 trillion dollars in 2021, while the damage in 2015 was “only” $3 trillion.
That's the total amount of money that we're all going to spend in one way or another to improve security. This includes recruiting experts and covering losses suffered by businesses and individuals. If so, how much do cybercriminals actually earn?
Cybercrime generates $1.5 billion of profits, while individual cybercriminals earn up to 521,000 dollars per year. And where do you think most hackers come from? Do you want to guess? And the winner is... China!
The R.P.C. is the home of cybercriminals, responsible for nearly 41% of all network attacks. Compare the income level we have just mentioned to the Chinese minimum wage of 161.07 to 348.02 dollars (different depending on the province) and you will understand that the lifestyle that computer piracy provides can be very tempting.
Here is the share of each type of attack in the $1.5 billion in profits:
2. Political or social motivation
Internet activists, also known as hacktivists, use technology to promote a political agenda or social change. It may seem innocent from an ideological point of view. However, most hacktivists seek and steal information that could harm their victim (s) or prevent the normal functioning of their target organization.
In the latter case, it is a DoS attack (Denial-of-Service, see below for more details), which can be considered one of the main cyberattacks. A good example of a denial-of-service attack is that of Estonia, which was hit in 2007 by massive waves of traffic aimed at various institutions. The result was the blocking of online banking, media, and government agencies. This attack was also considered to be an example of cyberwarfare. Often, hacktivists are hired to carry out such attacks, using botnet armies to achieve certain goals.
3. For the intellectual challenge
Most hackers, when asked, say it's the Reason no. 1 piracy. As you might expect, not all of these hackers are breaking the law.
That said, being able to execute different types of cybersecurity attacks and outsmart billions of dollars worth of corporations and governments might be more profitable on the wrong side of the law, for those who care about this stuff.
These are the top three motivations behind every cyber attack. We've covered the “Why.” Now let's take a look at the “Who.”
Who are the people behind these attacks?
We've all seen hacker movies like “Hackers,” “Swordfish,” and “Blackhat.” They help paint the image of the hacker as a lonely man in a dark hoodie.
You might already know it, but Hollywood largely romanticizes the hacker lifestyle to take advantage of it. In fact, this description only corresponds to a small percentage of hackers. On the contrary, the main actors behind major cyber attacks are:
- Organized criminals - The modern organization of large-scale cybercrime is more like a company than a few malicious individuals in a cellar. Like drug cartels, they are very agile and often more organized than the security experts who are trying to stop them. They are responsible for 50% of all violations in 2018.
- The initiates - More than a quarter of data breaches (28%) are the work of insiders. They are employees of a company or a public administration. This can happen unintentionally, even by installing infected malware from an email, allowing the cybercriminal to access the network.
- Nation-states - Nation-state actors know exactly what they are doing. Without the risk of lawsuits and with huge resources at their disposal, they can cause chaos abroad or be hired for espionage or propaganda purposes. State-affiliated actors are responsible for 12% data breaches.
- Hacktivists - These men and women are a particular breed of hackers. They are motivated by an ideology and they hack for a cause. One of the most famous hacktivist groups is “Anonymous.”
- Criminals - Not everyone is a team player. The most common cyberattacks are carried out by a single person. Statistics show that this is most often a young white man.
Who are the most common victims of cyberattacks?
In general, it can be anyone - individuals, businesses, or government institutions.
The sky is the limit for hackers. In the UK alone, almost half of businesses (43%) and 19% charities have experienced a cyberattack in the last 12 months. This percentage reaches 72% in large companies.
As far as individuals are concerned, more than 1.5 Millions of people are victims of cybercrime every day! And 65% Internet users around the world have been victims of various types of cyberattacks.
To make it easier for you, here is a table that shows you the most common targets of cybercrime:
Individuals represent 30% of all attacks, although the loot from these attacks is miniscule by comparison. This is easily explained by the fact that 1) it is easier to hack a person than a business and 2) the consequences of these attacks are much less severe than if a hacker is caught attacking an organization or government agency.
Types of cyber attacks
I have already mentioned the two main intentions of cyber attacks: 1) to paralyze or destroy a system or 2) to take control of the system and/or its data. Now we're going to break them down into more specific categories. Then we'll look at how each type of attack is carried out. We'll also look at what steps you can take to protect yourself and/or your business. Without further ado, let me introduce you to the different types of cyber attacks:
Malicious software
What is it?
Short for “malicious software,” malicious software is the main weapon in cyberattacks. It is designed to damage a system. Viruses, worms, Trojan horses, and adware are all examples of malicious software. They are capable of rendering the computer or the network inoperable or of giving access to the attacker.
How is it done?
In the past, malware was delivered manually to the system via a floppy disk or CD. Today, 92% of malicious software is delivered via email.
How do you protect your system from malware?
The best way to prevent your system from being infected with malware is to avoid spam emails. It is also useful to use a Antivirus program and to keep it up to date regularly. This will go a long way in making you immune to malware infections.
Phishing
What is it?
Phishing attacks are generally carried out by email, pretending to be a request from a trusted source (your bank for example). They provide a link to a fake site, often designed to be the real site. Unsuspicious users enter their personal information (username and password, for example) there, which is then stolen. 56% of organizations consider phishing attacks to be their top cybersecurity threat.
How is it done?
By email.
How do you protect yourself from phishing?
Be reasonable when reading your emails and browsing the web. Don't open attachments and links in emails that claim to be from trusted sources unless you're 100% sure they're legitimate. Another way to stay safe is to use a password manager, which can determine the vulnerability of the pages you visit. Finally, to avoid cyber threats, use the HTTPs protocol with sites that support it.
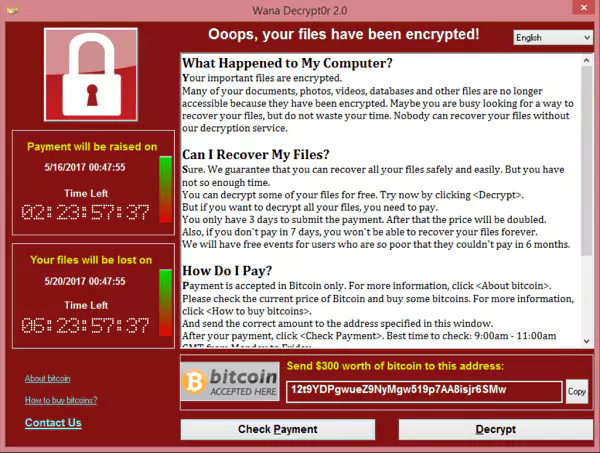
Ransomware
What is it?
It is malicious software that is used to lock users off their computers and prevent them from accessing their information until a “ransom” is paid. Generally, payment is made to an anonymous wallet via bitcoin or another cryptocurrency. More than 4000 Ransomware attacks happen every day, so be careful.
How is it done?
By clicking on compromised links in emails or social networks, or via drive-by downloads.
How do you protect yourself?
The best way is to minimize the effects of these cyber attacks. Back up your files regularly and use the tips I've given you above. Also, it is advisable to never pay the ransom if your computer is attacked.
Denial of service (DoS) attack
What is it?
These attacks aim to disrupt a network by sending huge volumes of traffic and data until the network is flooded and stops working. Its subtype - Distributed-Denial-of-Service (DDoS) - is created by an army of botnet computers that attack servers with overwhelming packets of data. The biggest example of such a network attack is the attack on GitHub, which decommissioned the site by sending 1.35 TB of data per second at its peak, when the site's average traffic was around 100 Gb/s.
How do you protect your website?
In general, it is very difficult to stop a DDoS attack once it has begun. Your ISP can help you by blocking traffic to your website.
There are also other attacks, such as the “man in the middle”, also known as eavesdropping. In this case, the criminal stands between you and the network you are connected to in order to steal data.
Another popular type of cyberattack is called Cryptojacking — when an actor uses the resources on your devices to mine cryptocurrencies without your knowledge. It installs hidden malware on your machine to do this. For information purposes, most attacks are carried out via email.
Summary.
The web is a tricky place to navigate. Given our dependence on the Internet, it is likely that the Third World War will take place entirely online.
Luckily, not all pirates are bad. White Hat Hackers are the opposite of criminal elements who carry out various types of cyberattacks.
Certainly, if cybercrime were a country, it would have the GDP of Russia. However, the world is investing more and more in cybersecurity. The success rate of targeted cyberattacks is now only 17% and keeps going down. And while this number is still worrying, it is an indication of things to come.
Hopefully, at this point, you have a general idea of what a cyber attack is and how to deal with it, if any.
Other useful reading:
FAQs
What is a cyber attack tool?
Cybercriminals use a wide range of tools to help them with their work.
The list includes web vulnerability scanners, password crackers, port scanners, etc. 90% of hackers also use some kind of encryption to cover their tracks. Blackhat hackers also create their own tools. Botnets are a great example of this technology.
Used primarily for DDoS attacks, botnets are essentially a network of infected systems, controlled by the criminal. Fortunately, the White Hat Hackers use the same tools to improve safety.
More and more businesses and people are also becoming aware of these threats, which is also very useful.
What is a disruptive cyber attack?
Disruptive attacks are deployed with the intent to disable critical business functions.
Ransomware, cryptojacking, and DDoS attacks are perfect examples of disruptive cyberattacks. DDoS attacks, in particular, could increase in the near future, given theIncrease in IoT devices.
The latter are almost tailor-made to be part of a hacker's botnet thanks to their poor security. Disruptive malware can have a long and lasting effect on businesses.
Fortunately, there are security platforms that can stop them in their tracks before they reach their destination.
What is cybersecurity?
Cybersecurity is the method of protecting programs, systems, or networks from a cyber attack.
This is a fast-growing sector, as there are also more and more cybercriminals. Digital security is expensive, but negligence is much more expensive.
Cybersecurity specialists are increasingly sought after around the world, and businesses are paying a high price. Are you considering your next job?
.svg)