Dive into the layers of TCP/IP, the backbone of online communication. Understand how it powers the internet and keeps us connected daily.
TCP/IP stands for Transmission Control Protocol/Internet Protocol, it's more than just a suite of protocols.
It's actually a set of standardized rules that facilitate communication between computers on a network, including the Internet.1. Each part of the acronym represents a distinct protocol, each of which has a crucial role to play in data transmission.
The combination of TCP and the IP protocol allows for efficient and reliable communication over the network, facilitating the many digital interactions we have on the Internet every day.
The protocol TCP/IP was developed in the 1970s by DARPA (Defense Advanced Research Projects Agency).
The origin of the TCP/IP model dates back to the 1970s, when a team of researchers led by Vint Cerf and Bob Kahn - often considered to be the fathers of the Internet - began working on ways to facilitate communication between different networks.

At that time, communication between computers belonging to different networks was a major challenge. Cerf and Kahn conceptualized the TCP/IP model to overcome this challenge, and their work laid the foundations for the modern Internet.
Adopted as a standard for the Internet, the model TCP/IP has played a crucial role in the development and expansion of the global Internet, transforming the way information is shared and accessed.
The power of the TCP/IP model lies in its simplicity and efficiency, allowing reliable and orderly communication between devices on a network.
Here's a closer look at the key components:
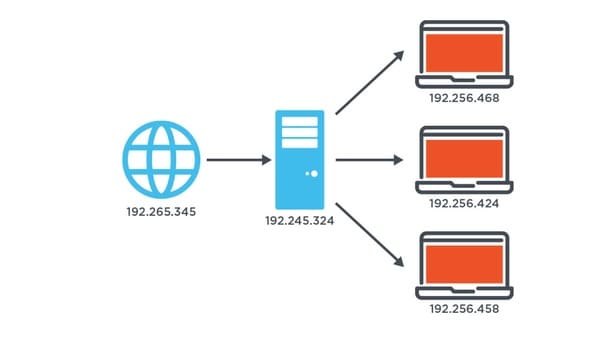
These protocols work together to ensure smooth and reliable communication over the network, forming the foundation on which the Internet is based.
The architecture of the model TCP/IP is often broken down into layers, each layer having a set of specific functions. There are four main layers in the TCP/IP model that facilitate communication on the network:
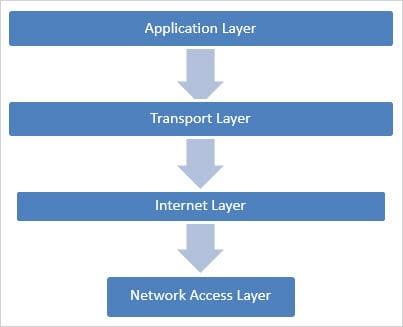
Application layer
Transport layer
Internet layer
Network Access Layer
When we dive into how the TCP/IP model works, we get to the thrilling heart of Internet communication.
Imagine TCP and the IP protocol as two inseparable comrades who harmoniously orchestrate the dance of data on the network.
The process involves several crucial steps, each of which is important in the smooth delivery of your data from point A to point B. Here is how these two accomplices operate:
The adventure begins with the Transmission Control Protocol (TCP), which takes care of the first crucial step: data splitting.
Let's say you have a message, picture, or video file to send over the network.
The TCP protocol (transport layer) takes this big piece of data and cuts it up into small, digestible pieces called data packets.
Each packet is labeled with crucial information like the source address, the destination address, and the sequence in which they need to be reassembled.
This step makes it possible to make the journey of data packets over the network manageable and efficient.
Now it's time for an IP (Internet Protocol) address to take over.
An IP address is the guide that navigates each packet through the vast labyrinth of the Internet.
It uses labels set by TCP (transport layer) to ensure that each packet takes the most efficient route to its destination, whether across the street or across the planet.
While packets may take different routes and arrive at different times, an IP address ensures that they all reach the correct destination.
Upon arrival, the TCP model (transport layer) takes over. He welcomes each package, checks the labels to make sure they have all arrived and in the correct order.
If a packet is missing or arrives late, the TCP model (transport layer) may ask to return it.
Once all the packets are received, the TCP model goes to work to carefully reassemble them in the correct order to reconstruct the original message, whether text, image, or video.
Once the message is successfully reconstructed, TCP sends a confirmation to the sender to report that the message was received undamaged.
This confirmation step is crucial as it assures the sender that their message has been received correctly, adding a layer of reliability to communication and performance.
In short, TCP and the IP protocol work hand in hand, one preparing and reassembling data, the other wisely guiding it through the network.
This smooth and orderly collaboration is what makes communication on the Internet both reliable and effective, allowing the sharing and exchange of information on the global web.
The TCP/IP protocol is not just a protocol, it's the protocol that makes the Internet work. Without it, the activities we take for granted on the web would be impossible.
Whether it's browsing websites, playing online, or streaming videos, it's the conductor who makes it all possible.
It is the invisible thread that connects all of our digital interactions, facilitating communication between Internet services like websites, online gaming, and streaming1.
Furthermore, the TCP/IP model also has a crucial role in the professional world. It facilitates communication between IT systems within businesses and between businesses, making e-commerce, remote working, and much more possible.
Security is a major concern in the digital world, and the TCP/IP model is no exception.
Although TCP/IP is not designed with security in mind, measures have been developed to address its security shortcomings.
Protocols like SSL (Secure Sockets Layer) and TLS (Transport Layer Security) work in concert with the TCP/IP protocol to provide secure communication over the network.
They encrypt the data transmitted, thus ensuring protection against eavesdropping and other security threats.
Additionally, mechanisms like firewalls and intrusion detection systems can be configured to monitor and control TCP/IP-based network traffic, providing an additional layer of security.
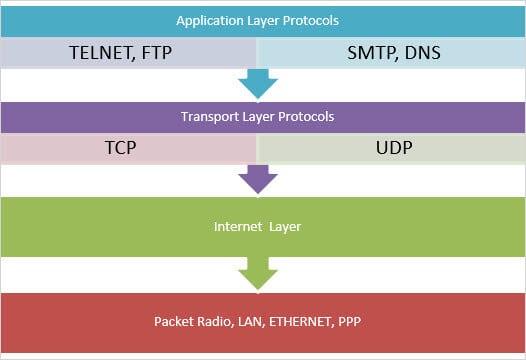
In the Internet protocol ecosystem, TCP/IP is often compared to other standards, each with its own advantages and disadvantages.
Below is a comparative analysis of TCP/IP with other common Internet protocols like UDP (User Datagram Protocol) and HTTP (HyperText Transfer Protocol).
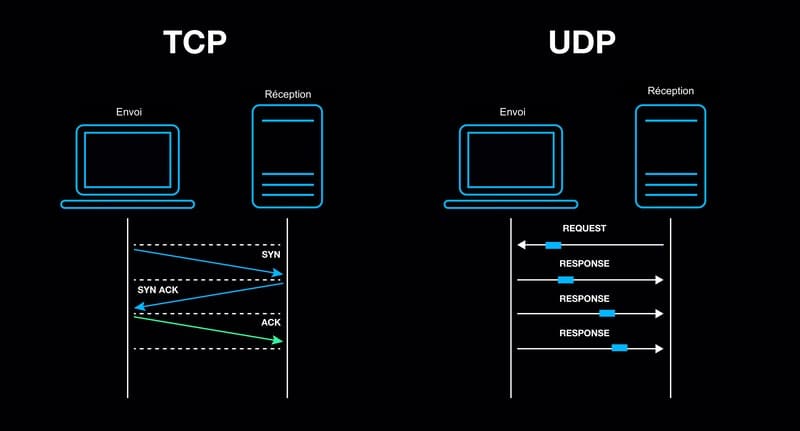
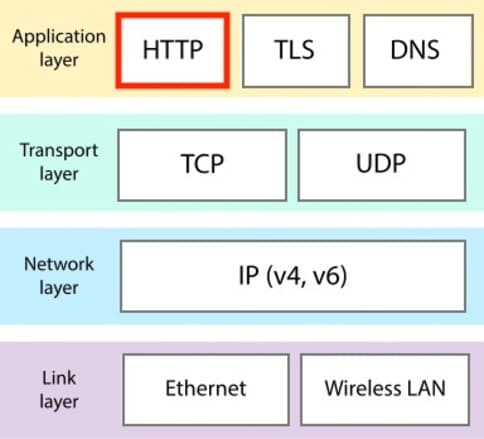
In short, TCP/IP is the foundation upon which other protocols, including HTTP, operate to provide various services on the Internet.
.jpeg)
In conclusion, although TCP/IP protocols and the OSI model aim to facilitate communication over networks, TCP/IP is often preferred because of its simplicity, ease of implementation, and widespread adoption.
OSI, on the other hand, while offering a more detailed structure, has not gained the same traction in the industry.

Wireshark is a very popular protocol analyzer that allows users to analyze data traveling across their network in real time.
It's incredibly useful for debugging network issues and for learning how TCP/IP works in a real-time environment.
Real-time packet capture and analysis.
Packet filtering to focus on specific protocols or IP addresses
Graphical visualization of the performance of network traffic data.
Support for over a thousand different protocols.
Wireshark is an indispensable tool for anyone who wants to deepen their understanding of TCP/IP and other networking protocols.
Its functional richness and its free use make it a preferred choice for network professionals.
Link below:
Get Wireshark

TCPDUMP is another powerful protocol analysis tool that operates on the command line.
It allows users to capture and analyze TCP/IP packets that pass through their system.
Capturing TCP/IP packets on the Internet
Filters to target specific packages.
Recording and reading captures.
Condensed or detailed display of packages and performance
TCPDUMP is perfect for users who are comfortable using the command line, offering powerful protocol analysis in a lightweight package.
Link below:
Get TCPDUMP

The SolarWinds Bandwidth Analyzer Pack is a professional solution that includes tools to monitor and analyze network performance and traffic.
Bandwidth monitoring and internet traffic analysis
Identification of network bottlenecks.
Real-time visualization of network traffic performance.
Customized alerts.
For professionals who need a robust solution to manage and analyze their network, the SolarWinds Bandwidth Analyzer Pack is a smart investment.
Link below:
Get SolarWinds Bandwidth Analyzer Pack
Although TCP/IP was not initially designed with internet security in mind, measures have been put in place to remedy its security shortcomings.
Protocols like SSL and TLS work in concert with TCP/IP to provide secure communication over the network.
Mechanisms like firewalls and intrusion detection systems provide an additional layer of security.